COS and TLS
TLS
COS Lite can be deployed unencrypted, with TLS termination only, or end-to-end encrypted.
Unencrypted COS Lite
The cos-lite bundle deploys COS with workloads communicating using plain HTTP (unencrypted).
TLS-terminated COS Lite
The traefik charm can function as a TLS termination point by relating it to an external CA (integrator) charm. Within the COS model, charms would still communicate using plain HTTP (unencrypted).
COS Lite with end-to-end TLS
The cos-lite bundle together with the TLS overlay deploy an end-to-end encrypted COS.
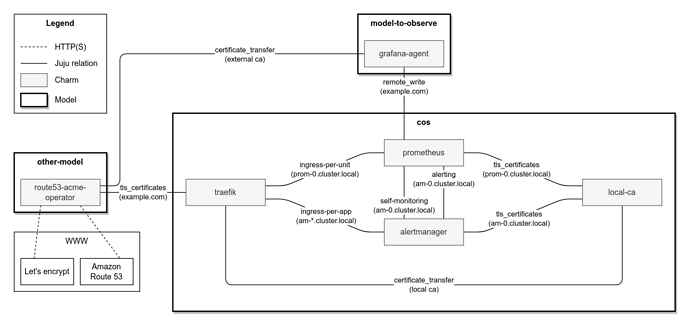
- COS charms generate CSRs with the k8s fqdn as the SAN DNS and the internal CA signs.
- All COS charms trust the internal CA by installing the CA certificate in the charm and workload containers, using the
update-ca-certificatestool. - The external CA provides a certificate for traefik’s external URL.
- Within the COS model, workloads communicate via k8s fqdn URLs.
- Requests coming from outside of the model, use the ingress URLs.
- Traefik is able to establish a secure connection with its proxied apps thanks to trusting the local CA.
Note: currently there is a known issue due to which some COS relations are limited to in-cluster relations only.
The end-to-end COS TLS design is described in the diagram below. The diagram is limited to prometheus and alertmanager for brevity and clarity.
As with any TLS configuration, keep in mind best practices such as frequent certificate rotation. See this guide for an example of monitoring certificates.
Last updated 10 months ago.